Effective Strategies for Prioritizing Vulnerability Remediation
Written on
Chapter 1: Introduction to Vulnerability Management
This article serves as a segment of my capstone blogging series, which chronicles the progress of my project. For a comprehensive list of articles, refer to my Cybersecurity Master’s Capstone archive. In this post and those to follow, I will refer to the organizations under analysis as Company A, B, C, etc., to maintain confidentiality.
Assuming you have already reviewed my Project Proposal, I will not reiterate the goals and objectives of my project or related information. If you haven’t done so, I recommend reading the proposal for essential context.
The preceding parts of this series (one through four) have covered various activities, including identifying threat actors and malware variants targeting Company A and its sector, gathering TTPs from historical cyber incidents, compiling a prioritized TTP ATT&CK matrix, and aligning a sample security toolset with that matrix.
In the fourth installment, I analyzed the gaps in the ATT&CK matrix and proposed mitigations for Company A, along with strategies for risk reduction in cases where complete mitigation is not feasible. In this article, I will conclude the project by utilizing Recorded Future to compile a list of priority CVEs, which will then inform reporting in a vulnerability management product to facilitate prioritized patching.
The threat profiling exercise has significantly aided the security operations team in assessing their strengths and weaknesses concerning the MITRE ATT&CK framework, particularly regarding priority threat actors and malware. While it is crucial to ensure that a security program can detect and prevent specific TTPs, it is equally important not to overlook exploitable vulnerabilities that can facilitate a cyber attack.
In this concluding phase of my project, I opted to leverage Recorded Future alongside my previously established Priority Threat Actor and Malware groups to pinpoint CVEs associated with historical cyber incidents. This step enhances our previous findings and provides actionable intelligence for the security team.
Throughout the earlier stages, the objective was to identify MITRE TTPs that the security team should focus on for detection and prevention. Now, we are taking an additional step to pinpoint which CVEs have been exploited by our threat actors and malware variants in the past, allowing for prioritized patching.
While threat actors may adapt their techniques from one attack to another, they often reuse the same exploits when possible. Thus, identifying previously exploited vulnerabilities enables an organization to safeguard its environment against the same weaknesses.
Compiling Priority CVEs
In Recorded Future, I initially gathered the CVEs associated with each priority threat actor group, ensuring not only a running list but also clarity on which vulnerabilities are targeted by which threat actors. Although some overlaps existed, understanding the weaknesses exploited by each group proved beneficial during the prioritized vulnerability reporting.
Below is the resulting Excel table:
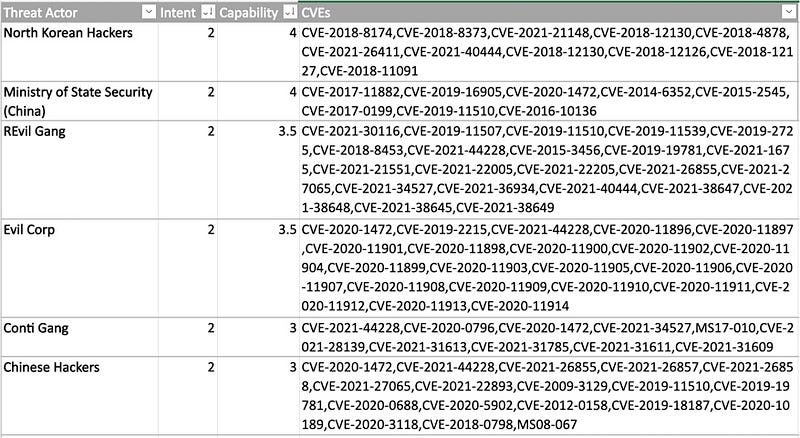
image by author
Next, I categorized my threat actor groups into "buckets" based on Capability and Intent scores, previously discussed in part one. Broadly, these scores reflect the sophistication of a threat actor (capability) and their level of intent toward Company A, its competitors, and the industry.
Based on these metrics, I established four categories:
- High Capability, Medium Intent — capability score of 3.5–4, intent score of 2
- High Capability, Low Intent — capability score of 3.5–4, intent score of 1
- Medium Capability, Medium Intent — capability score of 2–3.5, intent score of 2
- Medium Capability, Low Intent — capability score of 2–3.5, intent score of 1
Notably, there are no categories for High Intent, as the threat profile did not reveal any actors previously targeting Company A. Should any assessed company encounter such actors, a High Intent category would be necessary, as would a category for Low Capability actors if identified.
Creating a Dashboard for Vulnerability Prioritization
With the CVE list compiled and prioritization categories defined, the next step involves generating reports that illustrate the current threat landscape regarding Company A’s existing vulnerabilities.
While numerous display options exist, I chose four views:
- Counts of vulnerabilities in each bucket
- A graph illustrating vulnerabilities by Severity (as rated by the vulnerability management tool)
- Counts of vulnerabilities by threat actors
- Tables for each bucket displaying vulnerability descriptions sorted from highest to lowest
Here are some screenshots of the dashboard widgets described above:
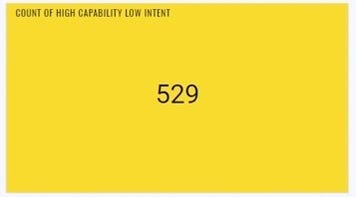
images by author
These widgets provide valuable insights into the exposure associated with Company A’s priority threat actors, further prioritizing high-risk vulnerabilities, particularly when examining the breakdown by capability/intent category and individual threat actor groups.
Additionally, a typical Red, Orange, Yellow color scheme was employed to indicate the severity of the vulnerability counts. The threat actor group widgets are dynamic, changing colors as the vulnerability counts fluctuate, aiding analysts in determining whether certain threat actor CVEs should be prioritized over others.
- Vulnerability count < 1,000 = White
- Vulnerability count < 10,000 = Orange
- Vulnerability count > 10,000 = Red
As this dashboard was primarily for project purposes, the thresholds were not exhaustively considered. For a production environment, a vulnerability analyst might implement additional colors to create a more nuanced threshold transition from White to Orange or adjust the Red threshold to a higher value.
Although I have only showcased a few snippets of the dashboard I created for priority CVEs, the value it offers to a security operations team should be evident.
Organizations often struggle to formulate effective vulnerability and patch management strategies, making it challenging to prioritize the multitude of vulnerabilities present in any environment. Threat intelligence aids security teams in narrowing the scope of the endless vulnerability list, leading to more effective prioritization.
Considering the components of the dashboard, there is potential for further refinement to create a more focused view based on the security team’s objectives. Additional filtering could highlight previously classified risky assets, outdated infrastructure, business-critical systems, and more.
This exemplifies how threat intelligence can complement risk management efforts, a topic I will explore in the sixth and final part of my Cybersecurity Capstone series.
Stay tuned for the concluding blog in my Capstone series, where I will delve into the interplay between risk management and threat intelligence-driven security operations, along with some final reflections.
Chapter 2: Video Insights on Vulnerability Management
In this video titled "Using a Risk-Based Approach to Prioritize Vulnerability Remediation," experts discuss effective strategies for assessing and prioritizing vulnerabilities based on risk factors.
The second video, "What Is Vulnerability Prioritization?" explains the importance of prioritizing vulnerabilities to enhance organizational security efforts.